When writing code or testing, it’s useful to have valid examples of whatever you’re working with for sanity checks. I need some example JWTs with accompanying private JWK and couldn’t find any, so I minted a few. I’m posting them here in the hopes they’re useful to others, too.

These keys were created using a fresh RS256 key. No other keys have been created using this key. Because the private part of this key pair is public — it’s literally right below, in plain text — remember that these keys should only ever be used for sanity checking and testing. In particular, never use these keys for production use cases!
Private JWK
{
"kty": "RSA",
"n": "0Vu_V2XethHpt12qWfLnWtsp3KVH_vwm0-ZzZ0qLrDnGo2zSXpup6YrkaHVbKYtr8hwJfea5JMt0Hf0rsXiWvXHRG-GK5B5soEzMEQtHQq9pwppS77289bNgUlYSesigB3vbWWPK28zmKt9cENPRX_prlN8M-8LwdqjTBT7JRlisGGwN7_YOxdfc7Jp33ITigtBpAbCcnQmi1j5ES4LEch0Qen2cH13hl6A5NEKU40PN5_qgZf4apR8peDkkG8rwWqomRK-H4ANgBoS6xV4l9hKSF_S9aepvoPgV1TT7hYyhIdsZYEktqmH_YCCSHLTbeGb0e7Q0UU7ADn0Mj4chdw",
"e": "AQAB",
"kid": "maLPWma3RT9nbZoxyBdFMCaKuwnkAy7qX-psOyRmKec",
"d": "Xf8r5wERX7ymKxJOSEljb2sEHhFFRGoQwsXunXseP8rG8RwMTbblMDqQd4ftULdM1WyaJGFhUfBY55gCNJG4WEFQSgzXL7mrOsOQQbzHF10rhliEkSgmvUf2oLENZfxKwWFuJ_HCpDIYSzpymwmHMWj9QV9t9GFfVl9RM0Mv2jloZ438Feww2tZFU27VEkigXQjpwHLvk_KCe6I6nrIHVIeCLFqDh23m22UTb-MMtmADB-N9xpZJMF6pct9qKi2MjqRBhkfkDlk9p4_D9h2BkvNlm_MWBykcrNd84vKgrvEJkOj5BwO2w8jJzHvrF4YZwcohEKK5MfonymU4tnSkvQ",
"p": "2SoWlNnqefPZDpuB0XLncj14VrRg88_l2DKRmUnjDGWzEJSGvgRwcJ8Nc9uXTiDqJVZmGvKt5Pn2emNZJD2-Cmdpbu3Jbu7CEJRC0cG6UecnvjQyItqaVYPp2WKEWrsXggQJGXNkEhIeFZoJRis2jkoIPomPtGjp0nbE6DNsdL0",
"q": "9sxLkQnltg4Qo9YMKkkLQGnxiWjNYcGZIvVhgSVVLNTKX-pO95jsxNWU4dTMu3b6aL2DBPOgz4AaTvB3OOWH3YN_-5nlTGXZRMFlPd1BOzehWoyDNa7NWzjbFMRNZ7d6-guVk78tb0uewGf6i8t6-b4U1pvMiHZ1Ea0qT1VCJEM",
"dp": "BWQpGVrrmkl2ewlbSLLckhZ6lVR3D7Z6k0p2GOMfsuAXePLnAXKkw_b-44BxGixxA6pIcKTTslqORu2Oefraa_GzSWC33nwo7zZvDjwL_xqI_wzWrczVhgf3V0E93e7FH6IwA6S8uEIg4xJm5ooOGaw21i6eFbGBFIuESet05tU",
"dq": "ce0a0Qg9lw3lFoxfr0FqxUBitGjBrme9NksJyKEgMYLFLQOvklJwsehaQumF3N_udl1NVwLT8BWVj20nzAcA8fubH90J4Xt-kWOpRaaWTyy9-lu00howR_T2BR8dEEy9oyGn2b09zwuca_tTyCaVTSY23l6rSy9LmW5Tgq27y5s",
"qi": "eVeQzkKqx-y-MR7B4dSRS4lM9cSQUtCjTIi-kHqZhM2ciNo997jrW0LHRk_AvQ4Efl-Yg20YD4gA2bK03KCK93DycDPckIMrToCYgmZ33a5v9Z14sFseIXmI--OgOnxEN-7QZ7eqPDXKXx_gKj74s4J3DJOrjJCAGIg8ikH_X8w"
}Example JWTs
eyJhbGciOiJSUzI1NiJ9.eyJqdGkiOiI1OTdkZWU3NC1jZDBhLTRhYmQtYTc2Zi05MTBjZWZhOTVkNmUiLCJzdWIiOiJhbGljZSIsImF1ZCI6WyJldmVyeW9uZSJdLCJoZWxsbyI6IndvcmxkIn0.XwmbtvHvu_lg3JIDpX5t0SmKsx-GIkbLkMV670aQRAyiXlztQdhc7O7jN1aYBZ9P1CLLXmEaaaD6vMqL6hqatLqmr3e5H9VEHOqDkJ_zNZf0YPT_qbQbraSjZ4tiaDZYL7AHJh9VtkZDHf9x77MVV6tZsfuBh11i1gbZVKNd9FcqcSG5kgppFf6kemqBzlWg-JQebDeEB0JxIXybSGqNMo9mW703E-JodWX-LicDSc1MTJqFhW6nk_DW3CRqN8xZ-OAfS7JYiwqB4Zf9VUbXhsNjhUDzJKROM7HS-CGkhENjx67RDlt3SNzKzAScVpD_8FtrHLIdN9VSVvTjbpApTw
eyJhbGciOiJSUzI1NiJ9.eyJqdGkiOiJhNDg4ZWYyYS1hMDhiLTQxMzEtYjI3ZS0zOTdmODdlNDExYjkiLCJzdWIiOiJib2IiLCJhdWQiOlsiZXZlcnlvbmUiXSwiaGVsbG8iOiJ3b3JsZCJ9.oIxBJUnShWqtpUYR1KxbOAeuXPs45s0kcI3s6pyZzG-aJkw9YJK7Zipv7qQZpFKwUcw-wZ3E3fQr9G_Bv0waYQM8OdekjECwpTby11c4138uqO7euozkRb0nhPmae7e2OJRacQVkzR8l1WMjJVhSsQi_I4VPvIwtSj-VLx9-A6lcEGenkGS5pHwQ2at6s54TQIr_kWa5_nwVDudw84jvM9i_mC0dkSpF1tu6tPfYF1iI8D0tQczy-UF24FZiZTBNFvH8je9ZX53sBLMMvkQJLGHQgbNh7h1egW4Q1qqysddFS5wRWZYuvkconiT-unMqnSNaJlczss6x9URG6XlFXA
eyJhbGciOiJSUzI1NiJ9.eyJqdGkiOiI5MDEyZGRmOC1lM2MyLTQ0OWMtYjI5MC0xNDcwMWU3MmNhZmQiLCJzdWIiOiJjaGFybGllIiwiYXVkIjpbImV2ZXJ5b25lIl0sImhlbGxvIjoid29ybGQifQ.b3FWB_2dJ4f6m4vvtTmfYTGEhU739DV3lCM20K8wQmnwgBk1rVj8oJ8Xr_3hjozoE2zdpBOUpjwgD2LBkP43gVzKSw2EyW6Y5a7fSrHhb9eRnWD94_OpbDpGaPS7RFs4FrbkRfm21Dqlced84wnnIDzjm8sHohYJnpEG_II9OhguE3g2e-wGZKz3u1J7Vo4ZOzlRc-yK8zM75xGEpGbRFMub298yeSM38EwLEp6EBFrmsvG-p6opd4acso6cMGBufHfqh3FRMXFuT4RaZ92nSmP_WS4lvwk4ueCgta09e6gD8E8cwHdPZBa1d7fV2TcHIyuha5vEofoAynY-9Pcy4QDissecting a JWT
There are many great resources online for dissecting JWTs, so I won’t go into great detail here. The following dissection of the first JWT (via jwt.io) unpacks the token and shows the relationship between the JWT and the JWK:
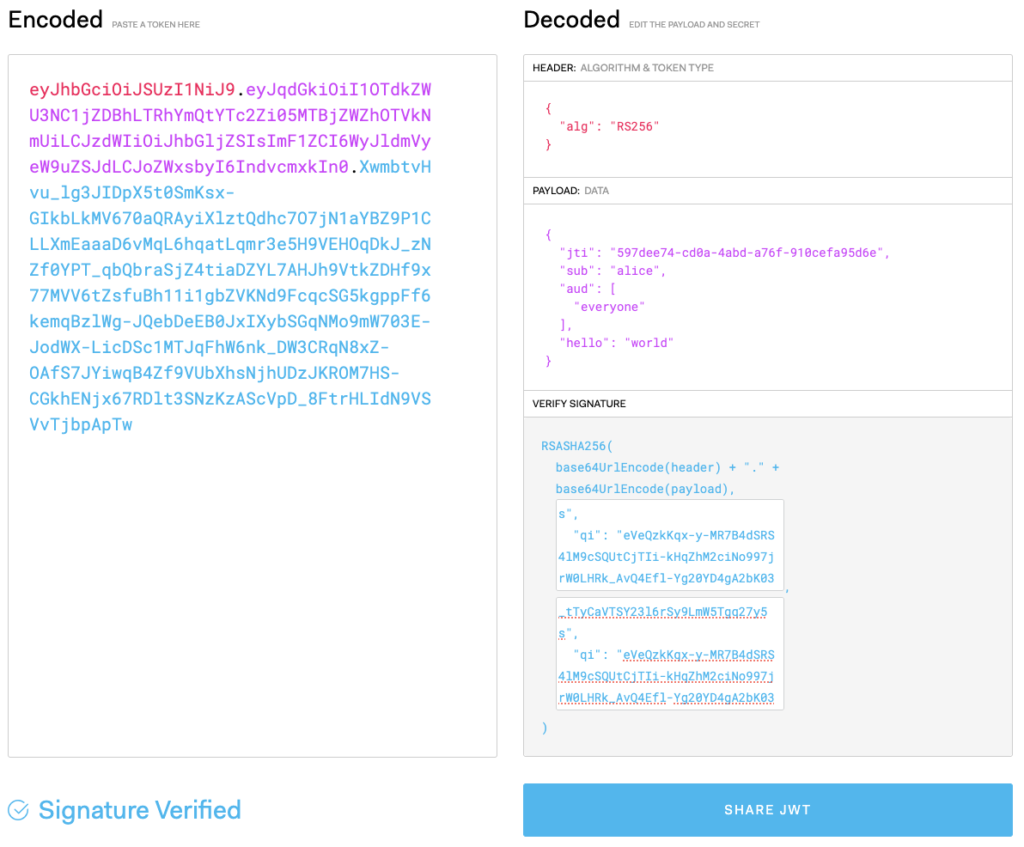
In particular, note that the algorithm is RS256 (as previously stated), the claims are available, and the signature verified using the above JWK as the public/private keys.
Generating More JWTs
For reference, here is the Java code I used to generate these keys:
KeyPair pair = Jwts.SIG.RS256.keyPair().build();
RSAPublicKey pubKey = (RSAPublicKey) pair.getPublic();
RSAPrivateKey privateKey = (RSAPrivateKey) pair.getPrivate();
RsaPrivateJwk privateJwk = Jwks.builder().key(privateKey).idFromThumbprint().build();
RsaPublicJwk pubJwk = privateJwk.toPublicJwk();
byte[] utf8Bytes = new JacksonSerializer<>().serialize(privateJwk);
String jwkJson = new String(utf8Bytes, StandardCharsets.UTF_8);
System.out.println(jwkJson);
System.out.println(
Jwts.builder()
.id(UUID.randomUUID().toString())
.subject("alice")
.audience()
.add("everyone")
.and()
.claim("hello", "world")
.signWith(privateKey)
.compact());
System.out.println(
Jwts.builder()
.id(UUID.randomUUID().toString())
.subject("bob")
.audience()
.add("everyone")
.and()
.claim("hello", "world")
.signWith(privateKey)
.compact());
System.out.println(
Jwts.builder()
.id(UUID.randomUUID().toString())
.subject("charlie")
.audience()
.add("everyone")
.and()
.claim("hello", "world")
.signWith(privateKey)
.compact());The Maven dependency GAVs are:
io.jsonwebtoken:jjwt-api:0.12.5io.jsonwebtoken:jjwt-impl:0.12.5io.jsonwebtoken:jjwt-jackson:0.12.5
